Ηοmo Digitalis in the first online webinar by EADPP Greece
On 17 June, at 18.00 CET the EADPP (European Association of Data Protection Professionals) Greece branch * holds its first online webinar entitled “Doing business online in social distancing era: privacy and communication issues”.
Mr. Konstantinos Kakavoulis will represent Homo Digitalis as a speaker in the webinar.
Participation is free.
The full schedule of the webinar:
“Doing business online in social distancing era: privacy and communication issues”
DATE: Wednesday, June 17th 2020
TIME: 19:00-20:00 EET / 18.00-19.00 CET
Introduction:
-Olga Tsiptse (Chairman GREECE EADPP Branch),
-Marc Vrijhof (Chairman EADPP)
Moderator:
-Dimos Kostoulas (General Secretary GREECE EADPP Branch)
Speakers:
-Dr. Nikos S. Panagiotou (Associate Professor, Google Research Scholar, Daad Scholar, Chevening Scholar, School of Journalism and Mass Communications, Aristotle University of Thessaloniki)
-Konstantinos Kakavoulis (LL.M. Lawyer specializing in International Law and Human Rights, Co-Founder and Board Member of Homo Digitalis)
*About EADPP: The EADPP is the 1st European Association for Data Protection Professionals. Its mission is to represent and support its members who are independent guardians of the GDPR. The primary aim of the organization is to facilitate, organize, structure, and represent European data protection professionals based on European perspectives and the principles of the GDPR. In this light, the first initiatives will be to create an EADPP certificate for data protection professionals and to secure proper representation at all relevant levels of the European Union. The EADPP is a not for profit run for and by its members.
Two strategic complaints of Homo Digitalis against the Greek Police
Homo Digitalis has filed 2 strategic complaints with the Hellenic Data Protection Authority (DPA). The complaints are directed against the Greek Police and concern the storage on its part in a central database of the fingerprints of all holders of Greek passports.
With its 2 complaints (reg. number. 3721/01-06-2020 & 3767/02-06-2020, respectively) Homo Digitalis examines the following sub-issues:
- The legality of the storage of fingerprints by the Greek Police in its central database and the refusal to delete such personal data.
The Police claims that Presidential Decree 178/2014 allows the storage of the fingerprints of all Greek passport holders in its central database. However, Homo Digitalis argues that the provisions of the Presidential Decree:
– do not refer to the storage of fingerprints in a central database,
– are not in line with recent strict legislation in the field of personal data, and
-do not provide the necessary safeguards to offset the risks of the rights of citizens holding Greek passports.
2. The delayed fulfillment by the Police of the right to information of the data subjects regarding the processing of their data and the way of exercising their rights.
The Police should have published on its website from the end of August 2019 all the necessary information set by Law 4624/2019 to inform what are the rights of data subjects and how these rights can be exercised in practice. However, EL.AS. published this information after 6 months. Homo Digitalis claims that this lack of information created confusion among data subjects about the ways in which they could exercise their rights and significantly delayed their submission of access requests to the Hellenic Post.
3. The representation of data subjects before the Hellenic DPA by civil society organizations, such as Homo Digitalis.
European law obliges EU Member States to allow data subjects to be represented by organizations such as Homo Digitalis when they consider that the protection of their personal data is being violated by police authorities. However, Greek law has not included the relevant provision. Homo Digitalis considers that this shortcoming is a significant violation of European law and acts as a deterrent to the protection of personal data of subjects.
The above two complaints are urgent due to the category of data that are being illegally processed by the Greek Police. (biometric data / fingerprints), as well as the large number of subjects involved in the illegal processing (total holders of Greek passports). Homo Digitalis asked the Hellenic DPA to consider the complaints as an immediate priority.
You can find a brief and understandable information in the form of illustrations regarding the specific complaints here.
You can read the detailed legal analysis regarding the specific complaints here.
This action was carried out completely voluntarily by a group of professionals and scientists, members of Homo Digitalis, without any funding from public or private bodies. If you want to support our actions you can do it here.
Open letter to the Transport, Telecommunications and Energy Council on DSA
On Thursday, 5/6/2020 the Center for Democracy and Technology sent an open letter to the Transport, Telecommunications and Energy Council of the Council of the EU, the Executive Vice-President of the European Commission, M.Vestager and the Commissioner for Internal Market, T.Breton as regards the upcoming legislative proposal on Digital Services (Digital Services Act – DSA).
Homo Digitalis co-signs the letter by the Center for Democracy and Technology along with other known civil society organisations, such as: Access Now, Article 19, Liberties, Civil Right Defenders, Digitale Gesellschaft, epicenter.works, HRMI, Justitia, The Peace Institute and Rights International Spain.
You may read the full text of the open letter in English here.
Contribution by Homo Digitalis to the video conference held by the Hellenic Competition Commission
On Wednesday June 3rd 2020 Homo Digitalis will have the great honour and pleasure of making a contribution on the topic “Algorithms and big data” to the video conference on e-commerce held by the Hellenic Competition Commission.
It is an extraordinary honour for our Organisation that the Competition Commission, having read the relevant memorandum and the proposals (link in Greek) we had submitted mid-May, invited us to participate by making a contribution to its video conference. We warmly thank the Commission for the invitation.
The video conference will present an excellent opportunity for us to elaborate on our positions and proposals as well as exchange ideas and opinions with the President of the Competition Commission, the Rapporteurs and the Investigation team of the Commission and the other contributors and participants of the video conference.
Once again, the praise goes to the editorial team of the relevant memorandum of Homo Digitalis which is comprised of our members: Vamvaka Elpida, Volikou Adamantia, Volikou Eirini, Gakis Dionysis, Konstantinou Stergios and Chelioudakis Lefteris.
Our President and member of the editorial team for the memorandum, Elpida Vamvaka, will represent us at the video conference.
Participation in the open consultation of the European Data Strategy
Homo Digitalis submitted today its positions and proposals to the European Commission on the European Data Strategy by participating in the relevant open consultation.
You can find our answers to the relevant questionnaire of the European Commission here, as well as the additional memorandum we submitted with our proposals here.
Deploying DP3T in the real world - how ready are we?
Undoubtably, there has been a big debate in the last couple of months around the topic of contact tracing apps. This debate focuses mainly on the choice of either centralized or decentralized architecture, in order to minimize the processing of personal data and make sure that privacy of participants is protected.
The teams still remaining in the PEPP-PT consortium are perhaps the main representatives of the centralized approach, having published the specifications of ROBERT on April 18, and of NTK the day after. On the other side, the teams in the DP3T consortium criticize centralized systems, pointing out that they can be turned into mass surveillance instruments of governments, and they emphasize on the development of the decentralized model DP3T. However, there have been several studies criticizing the privacy protection offered by decentralized models as well. In the decentralized approaches we should also include the protocol from Apple and Google, which will be soon in the OS of our mobile phones.
Understandably, all these discussions have created a lot of confusion to non-experts. In an effort to clarify some of the issues, we contacted Dr. Apostolos Pyrgelis*, Post-Doctoral researcher in EPFL and member of the DP3T team. In this article we publish his answers on our questions around the DP3T protocol, focusing mainly on how close we are to real-life deployment and the Greek reality. We would like to thank Dr. Apostolos Pyrgelis for his availability.
Also, we would like to thank our member Dr. Ioannis Krontiris** for reaching out to Dr. Apostolos Pyrgelis and the DP3T team and for facilitating this interview. We will soon publish this interview translated in Greek, as well.
1) What is the relation between Google/Apple platform (GACT API) and DP-3T? Is the plan to deploy DP-3T on top of the GACT platform or does it have its own independent access to the OS (e.g. Bluetooth hardware, storage of keys, etc.)?
The DP-3T project is formed by a group of international researchers whose interest is to ensure that proximity tracing technologies will not violate human rights key to our democratic society. It started independently of Google and Apple and remains independent of them. The DP-3T project is constantly making new proposals and is publishing positions to inform the discussion around proximity tracing. These positions may be different from these companies’ strategies or points of view.
The Google/Apple joint system design (i.e., the GACT API) aims at enabling interoperability for decentralized proximity tracing applications across iOS and Android mobile devices. This is particularly important for the success of contact tracing apps. To this end, the plan is to deploy the DP-3T protocol on top of the GACT platform and the DP-3T project has access to a code base for iOS and Android that is functional prior to the corresponding OS upgrades. Currently, DP-3T project members are working in close collaboration with Google/Apple engineers to provide open-source support for their API, since we expect that the majority of national applications will be built on top of it.
2) Broadcasting continuously Bluetooth beacons can be used to track people around, since one could try to link these messages together and create traces. What countermeasures do you take against this?
In the DP-3T system, the users’ mobile devices broadcast to their vicinity (random looking) ephemeral identifiers via Bluetooth Low Energy (BLE). To prevent user tracking via these broadcasts, the ephemeral identifiers are changing regularly (e.g., every 15 min). We here note that this is a shared feature among DP-3T and the GACT platform.
3) What is your experience and lessons learnt from testing the app with real users? How many manual tracers did you use for these tests?
We here clarify that we did not perform any testing of the application with real users or contact tracers. We only performed field experiments in known scenarios for which we could collect ground truth that would enable us to evaluate the accuracy of using BLE beacons for distance estimation among individuals, in various settings. A brief overview of these experiments can be found on the following video. We are currently processing the results of the field experiments aiming to identify the appropriate configurations and parameters for reliable distance estimation using BLE.
4) What would cause a false positive or a false negative in the DP-3T system? Consider for example thousands of people stuck in traffic in a busy city like Athens. That means I am in my car stopped for several minutes next to someone in their own car who’s infected. What existing measures are being considered to mitigate this class of problems?
First, we remind that traditional, person-based contact tracing has a lot of false positives since the majority of users that are exposed to infected others, do not present symptoms and do not get themselves infected. Similarly, it also has false negatives since infected users are unable to recall all the people that they met with in the recent past or identify strangers that they encountered in a bus, a shop, etc.
It is important to distinguish the above false positives/negatives from those that are related to contact discovery, i.e., the fact that two users were exposed to each other in close distance and for a specific amount of time (as defined by the public health authorities), when it comes to digital contact tracing. In the DP-3T system, the contact discovery process is realized via transmissions over Bluetooth, whose wireless broadcast nature is inherently affected by factors such as physical objects, radio interference, weather conditions, etc. This might lead to contact discovery false positives, e.g., if a contact is registered even though there is clear physical separation, such as a wall, between the users, and false negatives, e.g., if an actual contact is missed due to radio interference. The DP-3T team is currently performing extensive measurements to better understand the performance of Bluetooth communications for distance estimation in various settings and parameterize the application in a very conservative manner such that false positives/negatives are limited. We have not explicitly tested the traffic jam scenario, but to account for such situations the app will allow the users themselves to temporarily disable the contact discovery process.
5) Which factors are affected while deployment of DP-3T is scaled up? Would the protocol scale to the magnitude of millions of users?
The DP-3T protocol is designed in such a way that it easily scales to countries with millions of users without compromising their privacy. User devices need to download from the backend server minimal information per day (a few MBs) — which makes DP-3T also scalable to countries with poor broadband — and require very little time (a few secs) to generate their ephemeral keys and compute the infection risk of their owner.
6) Have you been approached by the Greek authorities regarding deployment of DP-3T in Greece? Do you have any indication in which direction Greece wants to take with respect to contact tracing apps?
We have not been approached by the Greek authorities regarding deployment of DP-3T in their country. As such, we do not have any information about the Greek plans with respect to contact tracing applications.
7) Assuming that Greece opts in for a decentralised solution in the future (DP-3T or other), what information would Greece have to share with other countries regarding visitors and tourists in order to achieve interoperability between decentralised solutions across countries? Would that reveal travel plans of people back to their homelands?
Interoperability of contact tracing systems across countries is a very important factor for their success — especially, in cases of free movement, such as the EU, where people travel daily to other countries for business, leisure, etc. The DP-3T project envisions interoperability between decentralized solutions across countries and is currently collaborating with designers and engineers from various countries to address its technical challenges. In one of the proposed interoperability solutions, users would have to configure their application to receive notifications from the countries that they travel into. Moreover, the homeland backend servers of the infected users would have to forward the relevant data to the backends of other countries that these users have visited. While this would reveal information about users’ travel patterns to their homelands, we believe that this is acceptable for the international success of contact tracing.
8) A major issue for contact tracing apps is persuading people to actually use them. Do you have any indication what is the minimum necessary penetration of the app to the population in order for the app to be effective? Is a high degree of case identification within a population required and does this translate to widespread testing?
Indeed, the success of contact tracing apps depends on users’ adoption and this is why we believe that it is of paramount importance to ensure them that their privacy is protected. While such a large scale deployment has never been performed before it is not clear what is the minimum necessary penetration of the app to the population for it to be successful. However, epidemiologists believe that any percentage of app usage will contribute to the pandemic mitigation efforts. To this end, the DP-3T project is hopeful that the app will have impact for “proximity communities”, e.g., commuters, co-workers, students, that have a suitable density of deployment. Finally, we remark that contact tracing apps should be complementary (and absolutely not a replacement) to traditional interview-based contact tracing and should be combined with public health infection testing policies. What really matters, at the end of the day, is to bring and maintain the virus transmission rate below 1.
* Dr. Apostolos Pyrgelis is a Post-Doctoral researcher at the Laboratory for Data Security of École Polytechnique Fédérale de Lausanne. His research interests include privacy-enhancing technologies and applied cryptography, and enjoys studying problems at the intersection of big data analytics and security or privacy. He received his PhD from University College London and his BSc and MSc from the University of Patras in Greece.
**Dr. Ioannis Krontiris holds a Ph.D. Degree in Computer Science from University of Mannheim in Germany, and a M.Sc. Degree in Information Technology from Carnegie Mellon University in USA, while he is also a graduate from the School of Electrical and Computer Engineering of the Technical University of Crete. He is currently working as a Privacy Engineer at the European Research Center of Huawei in Munich, Germany.
Online Shopping: Do we all pay the same price for the same product?
Written by Eirini Volikou*
On the same day, three people enter a book store looking to buy the book The secrets of the Internet. The book retails for €20 but the price is not indicated. The bookseller charges the first customer to walk in – a well-dressed man holding a leather briefcase and the new iPhone – €25 for the book. A while later a regular customer arrives. The bookseller knows that he is a student with poor finances and sells the book to him for €15. Finally, the third customer shows up; a woman who seems to be in a hurry to make the purchase. She ends up purchasing The secrets of the Internet at the price of €23. None of the customers is aware that each one paid a different price because the bookseller used information he deduced from their “profiles” to deduce their buying power or willingness.
In our capacity as consumers, how would we describe such a practice?
Is it fair or unfair, correct or wrong, lawful or unlawful?
And how would we react were we made aware that it targets us as well?
The above scenario may be completely fictitious but could it materialize in the real world?
In principle, the conditions in “regular” commerce are not such as to allow the materialization of our scenario. The obligation to clearly indicate the prices of products in brick and mortar stores directly and dramatically limits the traders’ freedom in charging prices higher than those indicated based on each individual client. In e-commerce, though, reality can prove to be strikingly similar to our fictitious scenario.
The e-commerce reality aka the “bookseller” is alive
Not infrequently it is observed that the indicated price of a good or a service on e-commerce platforms is not the same for everyone but divergences occur depending on the profile of the future customer.
Our online profiles are composed of information such as gender, age, marital status, type and number of devices we use to connect to the internet, geographical location (country or even neighborhood), nationality, preferences and consumer habits (history of searches or purchases) and so on.
This information is made known to the websites we visit via cookies, our IP address, and our user log-in information and can be used not only to show results and advertisements relevant to us but also to draw conclusions about our purchasing power or willingness. In other words, the role of the fictitious bookseller play algorithms that use our profiles for the purpose of categorizing us and automatically calculating and presenting to us a final price that we would be prepared to pay for the subject of our search.
This price may differ between users or categories of users who are often unaware of such categorisation or of the price they would be asked to pay had the platform had no access to their personal data.
This practice is often referred to as personalised pricing or price discrimination.
It is not to be confused with dynamic pricing in which the price is adjusted based on criteria that are not relevant to any individual customer but based on criteria relevant to the market, such as supply and demand.
The issue of personalized pricing surfaced in the public debate in the early 2000s when regular Amazon users noticed that by deleting or blocking the relevant cookies from their devices – which meant being regarded as new users by the platform – they could purchase DVDs at lower prices. The widespread use of e-commerce in combination with the rampant collection and processing of our personal data online (profiling, data scraping, Big Data) has since paved the way for the facilitation and spread of personalized pricing.
The experiment aka the “bookseller” in action
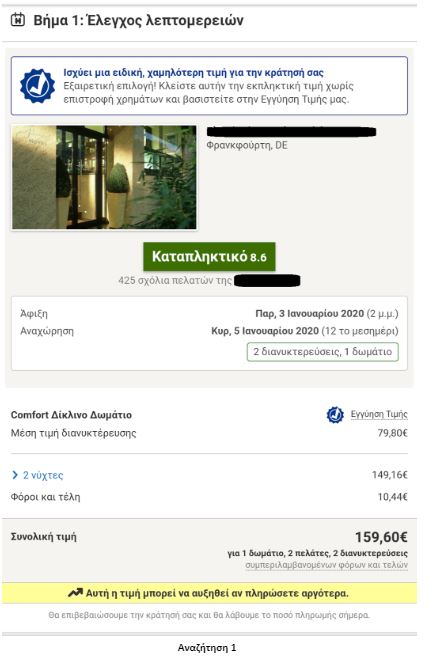
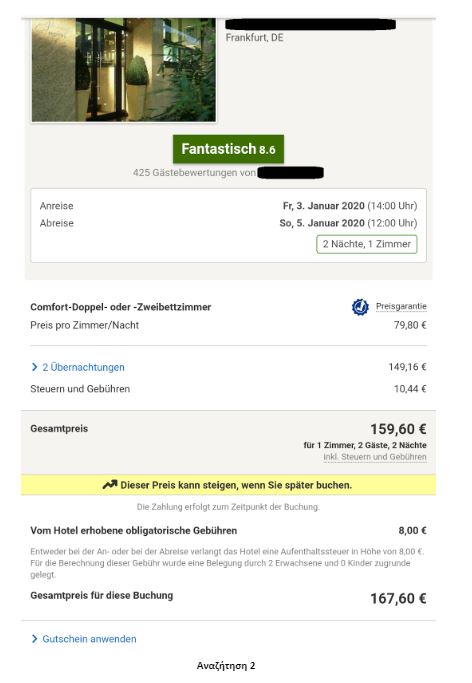
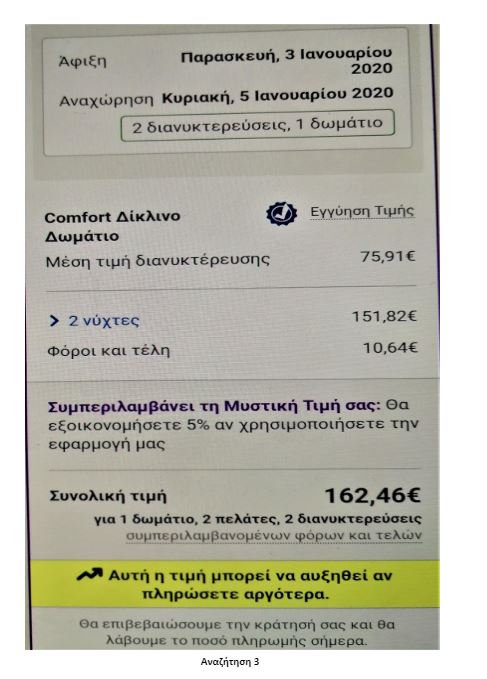
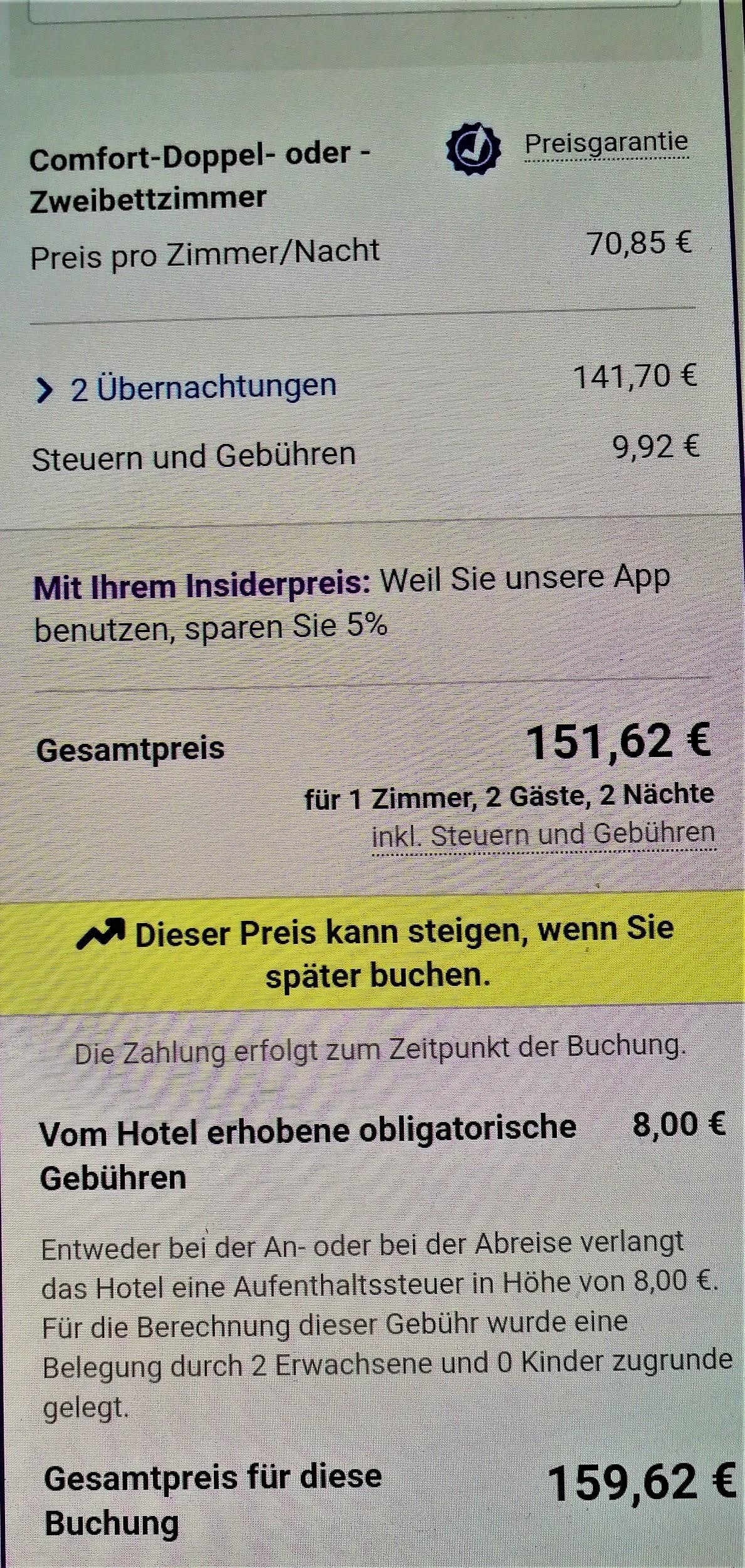
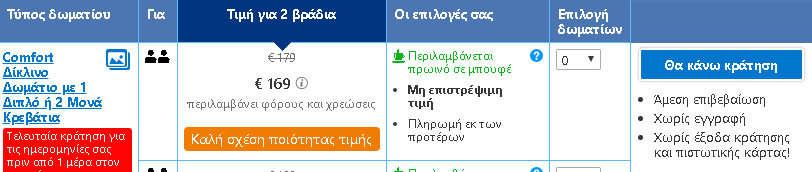
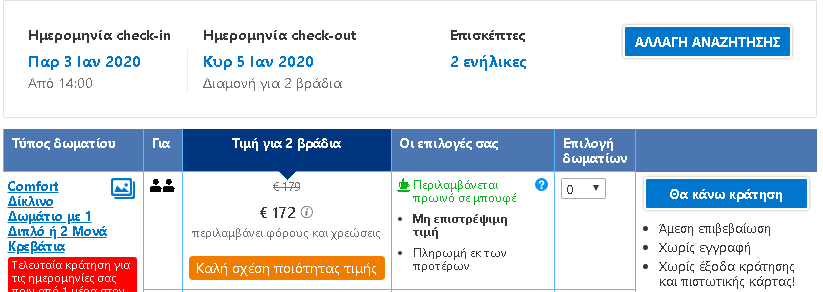
To put the practice to the test, consecutive searches and price comparisons were conducted on the same day (17/12/2019) for exactly the same room type (a “comfort” double room with one double or two twin beds) with breakfast for 2 travelers at the same hotel in Frankfurt, Germany on 3-5 January 2020. The searches were conducted on two different hotel booking websites and in all instances they reflect the lowest, non-refundable price option. The results are shown below:
Website Α
| Device | Browsing method | Website version | Price in € | |
| 1 | Τablet | Browser | Greek | 159,60 |
| 2 | Tablet | Browser | German | 167,60 |
| 3 | Tablet | Application | Greek | 162,46 |
| 4 | Tablet | Application | German | 159,62 |
Website Β
| Device | Browsing method | Website version | Price in € | |
| 5 | Laptop | Browser | Greek | 169,00 |
| 6 | Laptop | Incognito browser | Greek | 172,00 |
| 7 | Smartphone | Browser | Greek | 179,00 |
Search 1
Search 2
Search 3
Search 4
Search 5
Search 6
Search 7
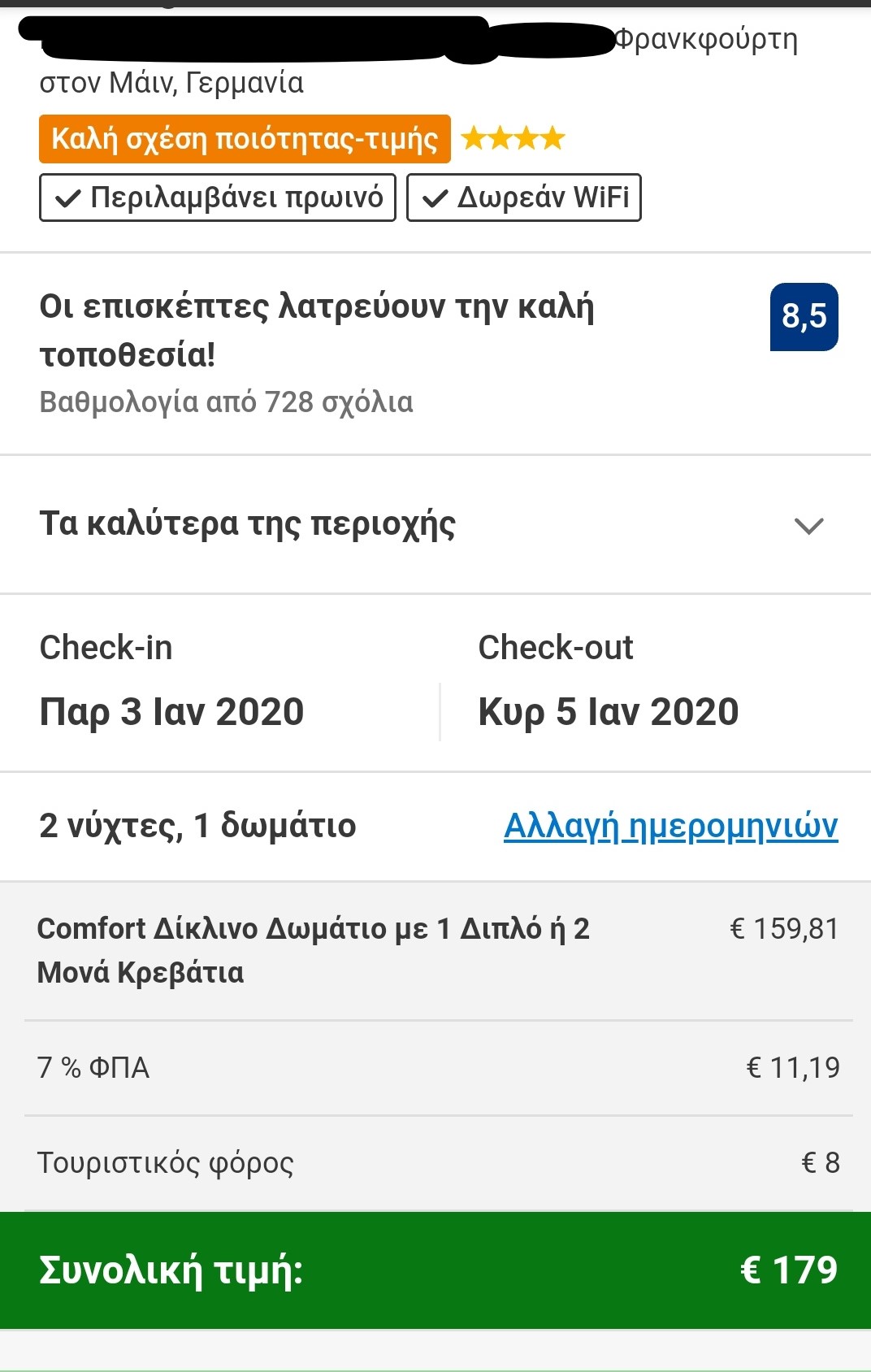
The search results show a range of different prices for the same room on the same dates.
There is a noteworthy price divergence depending on the consumer’s country or location. Even for the same country, though, the prices differ considerably depending on the type of device combined with the browsing method used.
All this information – or even the lack thereof in the case of incognito browsing – appears to play a role in the final price calculation and, hence, in the customized pricing for the users.
How is personalized pricing dealt with?
Personalised pricing, arguably, brings advantages especially for consumers with low purchasing power who benefit from lower prices or discounts and can have access to products or services that they could otherwise not afford. However, consumer categorization and price differentiation give rise to concerns because they are processes mostly unknown to consumers and obscure as to the specific criteria they employ.
At the same time, the use of parameters like the ones that appeared to influence the price in the hotel room experiment, i.e. country/language, device, and browsing method, does not guarantee a classification of purchasing power that corresponds to reality. What is more, research has shown that consumers, when made aware of the application of personalized pricing, reject this practice by a majority as unfair or unacceptable. This is largely true also in the event that personalized pricing would benefit them if they were also made aware that such benefit requires the collection of their data and the monitoring of their online or offline behavior.
When it comes to the legal approach to personalised pricing, different fields of law are concerned by it.
In the framework of data protection law, the General Data Protection Regulation (GDPR) does not explicitly regulate personalized pricing. Nevertheless, it provides that should an undertaking be using personal data (including IP address, location, the cookies stored in a device, etc.) it is obliged to inform about the purposes for which they are being used.
It follows that, if consumer profiles are being used for the calculation of the final price of a good or service, this should, at the very least, be mentioned in the privacy policy of the e-commerce platform.
The GDPR also requires consumer consent if personalized pricing has been based on sensitive personal data or if personal data is used in automated decision-making concerning the consumer.
From a consumer protection law perspective, traders can, in principle, set the prices for their goods or services freely insofar as they duly inform consumers about these prices or the manner in which they have been calculated. Personalized pricing could be prohibited if applied in combination with unfair commercial practices provided for in the text of the relevant Directive 2005/29/EC.
However, recently adopted Directive (EU) 2019/2161, which aims to achieve the better enforcement and modernization of Union consumer protection rules, will hopefully contribute to limiting consumer uncertainty and improving their position.
With the amendments that this Directive brings about not only is personalized pricing recognized as a practice but also the obligation is established to inform consumers when the price to be paid has been personalized on the basis of automated decision-making so they can take the potential risks into consideration in their purchasing decision (Recital 45 and Article 4(4) of the Directive). The Directive was published in the Official Journal of the EU on 18/12/2019 and the Member States should apply the measures transposing it by 28/5/2022.
It should be noted, albeit, in brief, that personalized pricing is an issue that competition law is also concerned with and, in particular, the possibility of charging higher prices to specific consumer categories for reasons not related to costs or for utilities by firms that hold a dominant position in a market.
In any case, staying protected online is also a personal matter.
At the Roadmap to Safe Navigation (in Greek) issued by Homo Digitalis, there can be found the behaviors we can adopt to protect our personal data while navigating through the Internet.
Consumers can adopt behaviors that help protect their personal data while browsing, such as using a virtual private network (VPN), opting for browsers and search engines that do not track users and using email and chat services that offer end-to-end encryption. To deal with personalized pricing, in particular, thorough market research, price comparison on different websites, or even different language versions of a single website, trying different browsing methods and, if possible, different devices can be a good start. It is important for e-commerce users to stay informed and alert in order to avoid having their profile used as a tool towards charging higher prices.
*Eirini Volikou, LL.M is a lawyer specializing in European and European Competition Law. She has extensive experience in the legal training of professionals on Competition Law, having worked as Deputy Head of the Business Law Section at the Academy of European Law (ERA) in Germany and, currently, as Course Co-ordinator with Jurisnova Association of the NOVA Law School in Lisbon.
SOURCES
1) European Commission – Consumer market study on online market segmentation through personalized pricing/offers in the European Union (2018)
2) Directive (EU) 2019/2161 of the European Parliament and of the Council of 27 November 2019 amending Council Directive 93/13/EEC and Directives 98/6/EC, 2005/29/EC and 2011/83/EU of the European Parliament and of the Council as regards the better enforcement and modernisation of Union consumer protection rules
3) Directive 2005/29/EC of the European Parliament and of the Council of 11 May 2005 concerning unfair business-to-consumer commercial practices in the internal market and amending Council Directive 84/450/EEC, Directives 97/7/EC, 98/27/EC and 2002/65/EC of the European Parliament and of the Council and Regulation (EC) No 2006/2004 of the European Parliament and of the Council (‘Unfair Commercial Practices Directive’)
4) Commission Staff Working Document – Guidance on the implementation/application of Directive 2005/29/EC on unfair commercial practices [SWD(2016) 163 final]
5) Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing Directive 95/46/EC (General Data Protection Regulation)
6) Poort, J. & Zuiderveen Borgesius, F. J. (2019). Does everyone have a price? Understanding people’s attitude towards online and offline price discrimination. Internet Policy Review, 8(1)
7) OECD, ‘Personalised Pricing in the Digital Era’, Background Note by the Secretariat for the joint meeting between the OECD Competition Committee and the Committee on Consumer Policy on 28 November 2018 [DAF/COMP(2018)13]
8) BEUC, ‘Personalised Pricing in the Digital Era’, Note for the joint meeting between the OECD Competition Committee and the Committee on Consumer Policy on 28 November 2018 [DAF/COMP/WD(2018)129]9) http://news.bbc.co.uk/2/hi/business/914691.stm
Homo Digitalis becomes full EDRi member
Today Homo Digitalis became full member of European Digital Rights (EDRi), the most prominent digital rights organizations coalition in the world!
We are the first Greek organization to make it and we are extremely happy to be representing our country.
Homo Digitalis had been an observer-member to EDRi since November 2018. Our actions for digital rights protection in both Greek and European level attracted the interest of champion digital rights organizations.
We warmly thank all our members for their contribution to our work during these years!
D3, the first Portuguese digital rights organization, also became full member on the same day.
Homo Digitalis speaks to ΕΘΝΟΣ about COVID-19 and related contact tracing apps
The President of Homo Digitalis gave an interview to journalist Mary Tsinu from ΕΘΝΟΣ about contact tracing apps, COVID-19, and the challenges that arise for human rights in the digital age.