Risk Management in the Digital World - A Chore or A Necessity?
Written by Ioannis Ntokos*
“Nothing in life is certain but death and taxes,” Benjamin Franklin (or someone before him) once said. But the phrase could well include another component, risk. “Death, taxes, and risk.” In the digital world, risks are a constant that we must take into account, whether as citizens, product or service providers, or as experts in the field of risk management. Let’s see how proper risk management can provide certainty and security in the digital space.
What does risk mean, and why does it deserve attention?
The digital world changes rapidly, every day. The concept of risk, however, is relatively static: every system, every program, every person using technology creates an “opening,” a vulnerability. These openings are not dangerous in themselves, but they are vulnerable to threats that can exploit them. Consider, for example, a flaw in a computer system at a nuclear power plant, a flawed process for accessing sensitive data, a bad setup of a network switch. The alarm bells are ringing.
The risk is there before you do anything, it is “inherent.” It is there by default, without any protective measures being taken. When you ride a bike, the very act of riding is a risk. In the digital world, the inherent risk arises from things like human carelessness, the complexity of systems, or the value of data shared with others. Risk itself is a certainty, a constant of life. That does not mean we ignore it.
So far, so good. The fact that I cross the threshold of my door every morning is a dangerous situation, theoretically. What is the point of action if the risk is there anyway? The next stage is to identify which risks require attention and action. This requires cold observation and logical thinking. Some risks are more significant than others, so they must go through the risk management "filter".
Calculating Risk
In its simplest form, risk (numerical or not) is simply a function of probability and impact. A given risk has (negative) consequences (impact) with some frequency (probability). Being able to quantify the variables of probability and impact in a quantitative way (using precise and detailed numbers, usually monetary for impact and annual occurrence units for probability) or qualitative way (using more arbitrary calculations, usually using a scale from 1 to 5) brings us closer to calculating risk.

In the example of cycling, a risk is my sudden encounter with a brown bear (and the unpleasant consequences that might follow). The likelihood of this happening varies depending on the situation - if I am riding my bike in an area of Korydallos, the chances of encountering a bear are close to zero. If I have gone cycling in the Pindos mountains, the situation changes dramatically. The impact of the encounter with the bear also changes. If I carry bear spray or have watched many videos on how to deal with a brown bear (the author of this article has watched quite a few such videos), I may escape with bruises and scratches (or a broken bicycle). If I lack knowledge and tools, things become more difficult.
Here the importance of protective measures and the transition from inherent to residual risk also becomes apparent. Through the protective measures at my disposal (spray), I can lower the impact of the encounter from certain death to admission to the hospital for stitches. Residual risk is the risk that remains after we take protective measures against it! Protective measures are an integral part of risk management.
Risk Management Methods
There are four appropriate ways to deal with a risk, once it has been perceived (and quantified or quantified). These options are: acceptance, transfer, reduction or elimination.
Acceptance means that you understand the risk and hold on to it, not passively or ignorantly, but rationally. Some risks are so small that it costs more to deal with them than to accept them. If I ride my bike downtown, I accept the infinitesimal chance (0.00001%) that a bear will attack me, and I enjoy my ride.
Transfer is the assignment of risk to someone else (usually through insurance). The risk does not disappear, it simply changes hands. The responsibility remains with the person subject to the risk, but there is coverage in case of damage due to the risk. In the bear scenario, I hope my insurance covers such attacks, or at least my family receives a lump sum (through my life insurance) in case the spray doesn’t help.
Speaking of spray, this is a risk reduction method! Reduction means that you limit the likelihood or impact, and it is the most common method of dealing with risks. This includes any form of preventive protection. Every protective measure I take aims to reduce the risk. If I’m out cycling in the Pindus Mountains with 10 other friends, the chances of the bear attacking me instead of one of them are drastically reduced!
Elimination is the most absolute option, as you move away from the risk and its source. Elimination is the final cleanup: the recognition that something is beyond “patching.” Are there many hungry bears on the mountain I’m planning to visit? I choose the sea instead of the mountain and I have peace of mind!
While the above ways of dealing with risk are all tried and tested, there is one reaction that is not legitimate - risk ignorance. Knowing the risk and consciously choosing to ignore it will inevitably lead to negative results!
Dealing with risk in the digital world
Risks similar to a random bear encounter exist in the digital and online space, only instead of hungry four-legged friends, we encounter hackers, abused platforms, the use of artificial intelligence that violates human rights and defective hardware. And with the same logic as our trip to the forest, these risks require special treatment, taking into account the following basic principles:
- Risk management is not a single event, but a cycle. You identify, assess, act, and regularly review. The digital world is constantly changing, which means that the risk landscape is also changing. What was secure in the morning may be vulnerable by evening. Technology waits for no one - and the associated risks must be constantly recorded and addressed.
- A holistic approach to risk is crucial. One gap is enough to cause radical damage to citizens, users, and businesses. Partial protection creates a false sense of security. In the digital space, the weak point is often not the most obvious. It can be the forgotten file, the inadequate password, the external partner using a fragile application. Therefore, a holistic view is required.
- It is also necessary to understand that risk is not only technical, but also organizational, human, or procedural. In practice, most damage results from mistakes, omissions, or misunderstandings. Technology simply exacerbates the consequences. Therefore, it is necessary to address it from many different angles.
- Awareness and education on information and data protection issues are key to reducing risks. No matter how organized you are, there will always be someone who will write their passwords in plain sight, open the wrong file, or accidentally press “delete.” The human element cannot be eliminated.
- Prevention is always cheaper than recovery. For the average user, risk management may seem like a chore, but the reality is that the world of technology has grown so much that ignorance of risk is costly. Just as no one waits to install an alarm system after a break-in, risk management works best before bad things happen.
The essence of risk management is targeted clarity: although absolute security is not possible, we strive for stability while trying to avoid major mistakes. When you understand this, risk management ceases to be a burden. It becomes an organized and coordinated effort, and then a habit. A kind of mental exercise where you ask: “What could go wrong? How much do I care? What do I do about it?” Not as an exercise in fear, but as an exercise in pure reasoning and protection. Risk will always be there. Managing it is a conscious choice, and awareness is a tool.
*Ioannis Ntokos is an IT risk management, information security and third party risk management specialist, with expertise in data protection. He specializes in ISO27001, NIST, NIS2 and the General Data Protection Regulation (GDPR). In his spare time, he offers career advice on IT governance, risk and compliance through his YouTube channel
We submit an Open Letter to the Prime Minister, calling on the Hellenic Republic to reject the Danish Presidency’s text on the CSA.
Homo Digitalis today submitted an Open Letter to the Prime Minister of the Hellenic Republic, Kyriakos Mitsotakis, regarding the proposed Regulation on Child Sexual Abuse Material (CSA Regulation).
In our letter — which we have also shared with the Minister of Justice and the Minister for Citizen Protection — we call on the Hellenic Republic to reject the Danish Presidency’s text in the upcoming vote at the EU Justice and Home Affairs Council on October 14, 2025.
The objective of the Regulation — to curb the distribution of child sexual abuse material — is right and necessary. However, the text proposed by the Danish Presidency would achieve the opposite effect, undermining security and trust in the digital space.
Specifically, 787 leading experts in communication security and encryption — including professors from top academic institutions in Greece — have emphasized that:
The technology for detecting child sexual abuse material is inaccurate and ineffective.
Mandatory scanning undermines end-to-end encryption and opens the door to mass surveillance.
The proposed technical measures can be easily bypassed by malicious users and threaten anonymity and freedom of information.
Real child protection comes through education and support for victims, not through mass monitoring.
On October 14, Greece’s position must be guided by knowledge, technical expertise, and the fundamental principles and values upheld by the EU Charter of Fundamental Rights and the Constitution of Greece.
You can read the full text of our open letter here.
You can also read a related article recently published on our website by our member Stergios Konstantinou here.
Learn more about Homo Digitalis’s work on this issue, including past meetings between our members — Haris Kyritsis, Haris Daftsios, Niki Georgakopoulou, Giorgos Sarris, and Angelina Barla — and Greek Members of the European Parliament, in cooperation with European Digital Rights (EDRi), here.
We spoke to NEWS247 about the data breach incident involving the Italian company doValue.
Homo Digitalis gave statements to journalist Eftychia Soufleri and NEWS247.gr regarding the hacking of the Italian company doValue, one of the largest loan management companies in Europe.
16 terabytes of personal data — that’s how much hackers claim to have stolen from the company’s systems, even posting an ad on the dark web to sell them. Our Co-founder and Executive Director, Eleftherios Chelioudakis, represented us by giving statements on the matter.
Find out more about here the sensitive personal data collected by debt collection companies, how much such data is worth on the dark web, and what the obligations of the doValue Group and its subsidiaries, including the Greek subsidiary doValue Greece, are — in case the hack also affected their systems, if the hackers’ claims prove true.
We would like to thank the journalist for including our statements in her article.
We submitted a FOIA before the Greek Ministry of Education for its Memorandum of Cooperation with OpenAI
At Homo Digitalis, we support the innovations brought by new technologies and believe that they can significantly contribute to the improvement of our society, provided that their use complies with the applicable legal framework and aims to promote and protect our rights and freedoms. We envision a better world, where the adoption of technological solutions is the result of critical thinking as well as informed and balanced decision-making.
In this light, we were concerned by the signing, on Friday, September 5, of the “OpenAI for Greece” Memorandum of Cooperation by the Ministry of Education, Religious Affairs and Sports with OpenAI and other stakeholders, for the pilot use of the ChatGPT Edu tool by teachers and students in 20 high schools across the country.
How will teachers and students feel when asked to use tools provided by a company such as OpenAI, which has already been fined €15 million for violations of data protection legislation in Italy and is currently under investigation for possible violations in other countries, such as Austria?
And on what grounds are Artificial Intelligence systems based on proprietary software from US tech giants being prioritized over equivalent tools that could be developed with free and open-source software by research centers and institutions in Greece? Such a choice disregards the European Union’s strategy to strengthen openness, transparency, and technological sovereignty, and, in the case of widespread adoption, will inevitably lead to the dependency of our education system on proprietary software and foreign companies.
In light of the above, today we submitted (protocol number 108260/8/92025) before the Ministry of Education, Religious Affairs and Sports a request for access to documents and information, in which we set out our concerns in detail and request access both to the Memorandum of Cooperation and to other related legal deliverables that should have been drawn up regarding the obligations arising from Law 4624/2019 and Law 4961/2022.
You can see our request here (EL).
Homo Digitalis’ participation in the final General Assembly and policy event of the EITHOS project
This week (2-3/9), Homo Digitalis Executive Director, Eleftherios Chelioudakis, LL.M, M.Sc participated online in the EITHOS EU Project policy event and their final General Assembly.
In his capacity as a pro bono member of the project’s External Advisory Board, Eleftherios contributed to the 3rd session, “Digital Education and Online Safety for Youth”. His presentation focused on the use of deepfakes of child exploitation material by youth, highlighting key provisions of the Greek Penal Code, and stressing how educational initiatives can play a crucial role in raising awareness about obligations and victims’ rights.
Moreover, he participated in the related consortium’s meeting with the External Advisory Board.
We warmly thank the organizers and the rest of the EAB members for their kind invitation and the smooth collaboration throughout the project’s implementation
European Digital Identity Wallet (EUDI Wallet): The Uncomfortable Truth Behind the Innovation
By Giannis Konstantinidis*
Note: This is the English translation of the original article which was written in Greek.
A critical look at the EU’s new “wallet” and the hidden risks it poses to personal data protection and privacy in the digital age.
What are digital identities?
Digital identities are the set of information (e.g. name, professional status, address, telephone number, password) that characterise us when we use digital services on the Internet. In simple words, they are our “digital selves” when we connect to social networking platforms, e-government services, e-banking systems, etc. In practice, digital identities contain personal data which in many cases are also sensitive (e.g. in the case of e-health services). Therefore, digital identities must enable fast and trouble-free access to digital services and meanwhile be accompanied by strict safeguards regarding information security and data protection.
How have digital identities evolved?
There are three main models for organising digital identities (Figure 1). In the centralised model, an organisation maintains a central database with the digital identities of all users. A key disadvantage of the centralised model is that users must maintain a separate account for each digital service they use. In contrast, in the federated model, organisations cooperate with each other and exchange digital identity information using a common protocol. For example, if a user has an account with a central provider (e.g. Facebook, Google, Microsoft or gov.gr), then they can log-in to another compatible digital service with the same information. Therefore, the federated model is quite easy to use, although the overall management of digital identities and their attributes is carried out by a few providers (who might be aware of the users’ activities).

Figure 1: In the centralised model, users have separate accounts (and passwords) for each service they use. In contrast, in the federated model, there are a few providers that act as single “gateways” to services. Finally, in the decentralised model, users use their digital wallets and ideally choose the specific information they want to share with service providers. (Creator Giannis Konstantinidis)
Therefore, in both the centralised and the federated model, a major concern is the concentration of a large amount of data in central locations that are considered attractive to malicious attackers (see massive data breaches). As an “antidote”, the decentralised model has been proposed, which is often associated with the concept of “self-sovereign identity” (SSI). In this model, the user controls all the identity elements that are to be used by the services. Instead of relying upon a few providers, each user holds a set of “credentials”, which have been issued by trusted entities, and maintains them in an application called a digital wallet or digital identity wallet. When the user needs to prove something (e.g. their age), the digital credential is directly presented (signed beforehand by a trusted organisation that serves as the issuer). Ideally, the presentation of that digital credential reflects the minimum amount of the required data and does not reveal the entire personal data of the user.
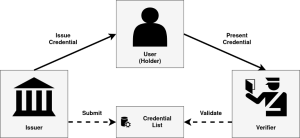
Figure 2: In the decentralised model, the issuer generates and delivers a credential to the user (holder) who stores it in the digital wallet. The user then presents the credential to a verifier, i.e. an organisation that requests confirmation of the user’s identity and/or status. The validity of the credential is verified based on the information found in a registry.(Creator Giannis Konstantinidis)
What is happening in the EU with digital identities?
With the revision of the eIDAS Regulation (2024/1183), the European Commission has established that each EU Member-State must offer its citizens a digital identity wallet. This will be an application for mobile devices in which each user will be able to store documents in digital form (e.g. ID cards, driving licenses, educational qualifications, social security documents and other travel documents). The user's interaction with the respective services will be done through the wallet, i.e. the user will select the credentials they wish to share. As mentioned earlier, the entire documents are not sent by each user, but a selected presentation of certain data in combination with the appropriate digital evidence that cryptographically proves the validity of those documents. Admittedly, the original vision of a “sovereign identity” seems to be significantly limited in the current design of the EUDI Wallet. In particular, the draft architecture (i.e. Architecture and Reference Framework - ARF) foresees the use of a traditional Public Key Infrastructure (PKI). Simply put, instead of leveraging a fully decentralised system, the European Commission chooses to leverage existing infrastructures that collect digital identity data. As such, it is more of a cross-border federated model in which users are responsible for managing and sharing their credentials on their own, rather than a fully decentralised model.
Is the protection of privacy and personal data enhanced or undermined?
Based on current developments, several risks related to data protection and privacy arise. First, the wallet can generate unique identifiers for each user (although theoretically this is necessary to identify the user when accessing cross-border services in the EU) and several experts express fear that these identifiers will allow for the continuous monitoring and correlation of all user activities.
In particular, according to the position of a group of distinguished academics (specialists in cryptography), the proposed architecture does not include sufficient technical measures to limit the “observability” and prevent the “linkability” of user activities. This means that even if user activities are carried out through the use of pseudonyms, there is no special care to prevent service providers from collecting usage patterns and correlating them with each other. So, in practice, this gap allows the tracing of user activities. The latest version of the architecture (ARF 2.3.0) recognises these risks, however, the integration of appropriate mechanisms remains at the level of discussion and has not yet been implemented (due to complexity and certain technical limitations). The European Telecommunications Standards Institute (ETSI) recognises the importance of technical measures, such as zero-knowledge proofs (ZKPs), but it is shown that (for the time being) the complete elimination of tracking is not feasible due to the technical complexity and lack of interoperability.
Regarding the overall “flexibility” and accountability of the ecosystem, there are also several negative comments. For example, if a service decides to request more data than necessary, there is no mechanism for prevention or even control. At the same time, it is considered that a huge share of responsibility will be shifted to users, because they will be constantly asked to approve the credentials that will be shared with service providers. In fact, if something goes wrong (e.g. in the event of theft of the user’s device or electronic fraud), there are no sufficient protection measures and therefore the user bears a large share of the responsibilities. In fact, there is no provision (so far) for any kind of recovery or restoration process.
Finally, an additional concern relates to the expansion of the wallet's functionalities, as it is going to gradually collect all kinds of electronic documents and certificates (e.g. even travel credentials and electronic payment details). Thus, the risk of a "surveillance dossier" emerges, where a malicious analyst or attacker could discover an extensive set of information about a person through a single medium.
Towards a cautious acceptance or questioning of the framework?
Although the EUDI Wallet is an important step in the development of modern digital services on the Internet, it comes with several challenges. If citizens are to trust such a technological solution, they must do so with full awareness of the advantages as well as the potential risks involved. At the same time, experts must further develop and document the mechanisms that contribute to security and privacy, otherwise we risk moving from a “wallet that empowers users to protect their data” to a “wallet that exposes data arbitrarily”. Finally, the contribution of experts and civil society organisations is extremely important, as gaps and possible omissions can be identified and corrected before the final implementation.
*Giannis Konstantinidis (CISSP, CIPM, CIPP/E, ISO/IEC 27001 & 27701 Lead Implementer) is a cybersecurity consultant and member of Homo Digitalis since 2019.
Homo Digitalis spoke at the 2nd International Conference of ATI dedicated to Democracy and Social Justice.
Homo Digitalis participated in the 2nd International Conference of the Alexis Tsipras Institute
Konstantinos Kakavoulis joined academics, professionals, politicians, and activists from Greece, the European Union, and the United States. He spoke about the need to strengthen the protection of digital rights in modern democracies, on a panel that attracted great interest. Among the distinguished speakers at the event were Bernie Sanders, Michael Sandel, Jeffrey Kopstein, and many others. The speech is available at the link here.
We warmly thank the organizers for the invitation and for the excellent discussions we had during the event!
Homo Digitalis at the 2nd International Conference of ΑΤΙ dedicated to Democracy and Social Justice
Homo Digitalis will participate in the 2nd International Conference on Democracy and Social Justice, taking place on June 10 at 15:00 at the Nikos Skalkotas Hall of the Athens Concert Hall, organized by the Alexis Tsipras Institute!
Our organization will be represented by Konstantinos Kakavoulis, Co-Founder of Homo Digitalis & Lawyer, who will deliver a speech in Thematic Session II: “Democracy and Digital Transformation.”
Also speaking in the same session:
Evagelia Emily T., Assistant Professor and Researcher at the McCourt School of Public Policy, Georgetown University
Elisavet Linos, Associate Professor of Public Policy and Management, Harvard Kennedy School of Government
Kostas Gavroglou, former Minister of Education, Research and Religious Affairs (2016–2019)
Christos Porios, Founder of Schema Labs & Open Council
You can find more information about the conference, registration, and the full program – which features internationally renowned and highly respected speakers – here.
Homo Digitalis successfully delivered its talk at CPDP2025
Two weeks ago Homo Digitalis participated again at Computers, Privacy and Data Protection Conference, speaking at the Panel “Protecting the Digital Rights of Asylum Seekers and Refugees”, organised by the Centre for Fundamental Rights – Hertie School!
Eleftherios Chelioudakis, from our team joined Francesca Palmiotto (IE University) , Derya Ozkul (University of Warwick) and Joanna Parkin (EDPS – European Data Protection Supervisor) on Friday 23.05, at the closing panel of the conference in Grande Halle!
You can read the full recap of our panel discussion here.
Congratulations to the team of organizers from Hertie School, Ida Reihani, for their great efforts and cooperation!








